Exemplary instructions on how to install the Certum SSL certificate on servers
Apache – Installation SSL certificate and intermediate certificates
In order to install an SSL certificate you need the following files:
- the file containing the server certificate: yourDomainName.crt,
- the file containing the private key,
- the file containing the intermediate certificates (intermediate/ca-bundle) relevant to the ordered SSL certificate.
After receiving information from Certum about the issued certificate, the certificate file will be available for download from the user account in the Data security products tab.
Copy the entire certificate content from the line —– BEGIN CERTIFICATE—– to —–END CERTIFICATE—– and save it to the mojadomena.crt file.
Download ca-bundle based on the function of the SHA-2:
- for Commercial SSL – DVSSLChain-SHA2.crt
- for Trusted SSL – OVSSLChain-SHA2.crt
- for Premium EV SSL – EVSSLChain-SHA2.crt
Place the file on the server which makes your website available, in the relevant directories.
Usual settings:
- the previously generated ssl.key private key needs to be placed in the /etc/ssl/ssl.key directory. Note: Only Apache can have access permission to this directory.
- The yourDomainName.crt and ca-bundle files should be moved to /etc/ssl/ssl.crt directory.
Important: The above paths serve only as examples. Your server may have different ones — some modification may be required.
Edit the SSL configuration file for the web server with a text editor.
Important: This file location varies depending on the web server configuration.
For Apache server:
- Fedora/CentOS/RHEL: /etc/httpd/conf/httpd.conf
- Debian and Debian based: /etc/apache2/apache2.conf
Common file names for SSL configuration:
- httpd-ssl.conf
- ssl.conf
- or in the directory: /etc/apache2/sites-enabled/
In the VirtualHost configuration of the website to be encrypted, you should add (if there are none) the following entries:
- SSLEngine on
- SSLCertificateKeyFile /etc/ssl/ssl.key/server.key
- SSLCertificateFile /etc/ssl/ssl.crt/yourDomainName.crt
- SSLCertificateChainFile /etc/ssl/ssl.crt/yourDomainName.ca-bundle (with Apache 1.x SSLCertificateChainFile instead of SSLCACertificateFile should be used)
Important: The above paths serve only as examples. Your server may have different ones — some modification may be required.
Additional configuration:
- SSLProtocol all
- in Apache 2.4 enabling SSLv3 and TLSv1 protocols and optionally TLSv1.1 and TLSv1.2 (in OpenSSL 1.0.1 and higher).
- in Apache 2.2. a SSLProtocol All -SSLv2. directive should be used. The -SSLv2 parameter disables the obsolete SSLv2 protocol support.
- SSLHonorCipherOrder On – server enforcement of the ciphers use order
- SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS – setting priority for the strong ciphers while at the same time disabling the weak and obsolete ones.
Save changes to the configuration file
Restart the server with the following commands:
- Debian or Ubuntu distributions: /etc/init.d/apache2 restart
- Red Hat/Fedora/CentOS distributions: apachectl restart
- other commands: /usr/sbin/httpsd restart or /etc/init.d/apache restart.
IIS 8 – Installation SSL certificate
IIS 8.0/8.5 — Installation SSL certificate
Download the certificate file (serial_number.cer) from your user account in the Data security products tab
In order to “close” previously generated CSR requests on the IIS and upload the SSL certificate received, go to the Internet Information Services (IIS) Manager, and from the left menu select your server name. In the center panel click the Server Certificates icon, then in the Actions right-hand panel select Complete Certificate Request.
Select the file that contains the server certificate issued. In the Friendly name: box enter a friendly name for the certificate, which will help you to identify it, e.g., www.your-domain.com. Confirm it with the OK button.
The issued server certificate will be displayed in the Server Certificates center panel.
Linking the certificate to a website:
- Click on the website name (Default Web Site), then from the Actions menu select Bindings…
- In the Site Bindings window which will be displayed click Add….
- In the Add Site Bindings window from the Type: dropdown list select https, then from the SSL certificate: on dropdown list select the certificate which you will use for your website. The list displayed includes certificates with their own private keys
- Confirm changes
MMC console configuration:
- Launch the MMC (Microsoft Management Console) console. From the File menu select Add/Remove Snap-in…
- Then, from the list of available snap-ins, select Certificates and click on the Add > button
- Select Computer account and click Next.
- Select Local computer and click Finish.
IIS – Installation of intermediate certificates
Intermediate authority certificates are very important for the SSL certificate to work correctly. They should be installed on the web server, so that the web browser can verify the SSL certificate issuer in the correct manner.
Note: Actions described in this manual should be performed only if there are no certificates installed on the Windows 2008/2012 server system.
For certificates that support the SHA-2 algorithm, download the following intermediate certificates:
- For a Commercial SSL certificate or its MultiDomain/Wildcard option, the following intermediate certificate should be downloaded and installed on the server:
Authority key — Certum Domain Validation CA SHA2 (the key is available in different formats):
- For a Trusted SSL certificate or its MultiDomain/Wildcard option, the following intermediate certificate should be downloaded and installed on the server:
Authority key — Certum Extended Validation CA (the key is available in different formats):
- For a Premium EV SSL certificate or its MultiDomain/Wildcard option, the following intermediate certificate should be downloaded and installed on the server:
Authority key — Certum Extended Validation CA (the key is available in different formats):
Installation of intermediate certificates on a server — step by step
Press the [Windows+ r] key combination and enter the mmc.exe command. The MMC Attachment editor will open. From the File menu, select Add/Remove Snap-in. In the new window, click the Add button and then point to the Certificates attachment and press the Add button.
From the Certificates (Local Computer) tree expand the Intermediate Certification Authorities branch. Select the Certificates item, right-click and from the menu select All Tasks -> Import…
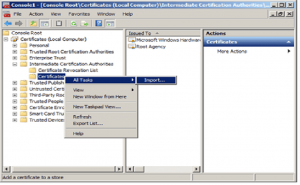
In the Certificate Import Wizard click Next.
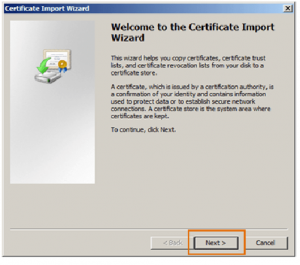
Select the file with an intermediate certificate and click Next.
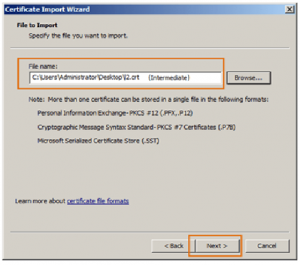
Select a target location where the certificate will be stored. Select Place all certificates in the following store. The Certificate store: box should indicate Intermediate Certification Authorities.
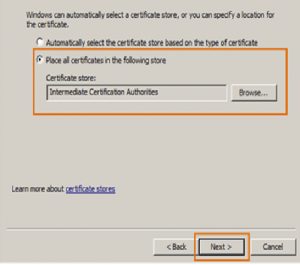
Select the file with an intermediate certificate and click Next.
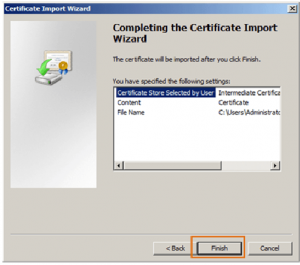
If you want to install intermediate certificates for certificates of other types, repeat the above steps (from points 2 to 6).
NOTE:
In some cases changes in the IIS configuration may not be visible after the service restart. If this is the case, you should restart the Windomessws operating system.